ISM6045 Current
Economic & Social Implications of Information Systems Syllabus
FALL 2005
Course
Description: |
 The
Business Community has finally realized that managing Information
Technology should no longer be left solely in the hands of the
IT department. There must be collaboration across the various
departments otherwise the system that is supposed to serve you,
the user, becomes a system dominating, you, the user. The Business
Community must now learn enough about IT to be able to take informed
decisions that directly concerns his/her organization, his/her
department, and his/her business. Do we need e-Commerce? If we
do, then we need to look at Digital Certificates, Digital ids,
SSL, Shopping carts, accepting online payments and much more.
If we work on a network, we have to look at how networks function,
who needs to be given access to what information and how do we
protect this data? What are redundant systems? What is RAID 5?
What are Access Controls? The data that the company possesses
how should that be protected? Should we use Symmetric or Asymmetric
Encryption? Are we planning a new system? What is the cycle of
Systems Analysis and Design? Do we have an old system? What is
a legacy system? Finally what is 18 USC 1030? How do the legal
aspects affect us? We need to address all of the above at the
Corporate Level, not solely at the IT Level. It is therefore imperative
that we, the Business Decision Maker, become acquainted with the
terminology, the concepts and gain experience in this world of
IT jargon. This is where we start. Good Luck. The
Business Community has finally realized that managing Information
Technology should no longer be left solely in the hands of the
IT department. There must be collaboration across the various
departments otherwise the system that is supposed to serve you,
the user, becomes a system dominating, you, the user. The Business
Community must now learn enough about IT to be able to take informed
decisions that directly concerns his/her organization, his/her
department, and his/her business. Do we need e-Commerce? If we
do, then we need to look at Digital Certificates, Digital ids,
SSL, Shopping carts, accepting online payments and much more.
If we work on a network, we have to look at how networks function,
who needs to be given access to what information and how do we
protect this data? What are redundant systems? What is RAID 5?
What are Access Controls? The data that the company possesses
how should that be protected? Should we use Symmetric or Asymmetric
Encryption? Are we planning a new system? What is the cycle of
Systems Analysis and Design? Do we have an old system? What is
a legacy system? Finally what is 18 USC 1030? How do the legal
aspects affect us? We need to address all of the above at the
Corporate Level, not solely at the IT Level. It is therefore imperative
that we, the Business Decision Maker, become acquainted with the
terminology, the concepts and gain experience in this world of
IT jargon. This is where we start. Good Luck.
Course Catalogue Description
Introducing concepts/software in enterprise-wide computing, information
architecture, process analysis/design, data models, client/server
computing, information security and network survivability.
Course syllabus
Introducing concepts in enterprise-wide computing, information
architecture, process analysis and design, data models, client/server
computing, information assurance and management and maintenance
of laptops and PCs.
Provides extensive usage of available PC software for business
decision making,
data management, project management and presentations.
Understanding e-commerce secure transactions as well as secure
transmission of digital data.
Usage of software for creating digital ids, digital signatures,
digital certificates and encryption.
Understanding transmission media and how digital data moves through
LANs, WANs, VPNs and the Internet.
Implications of different types of attacks on information systems,
and preparation and analysis of network survivability for the
business manager.
|
Course
prerequisites: |
Prerequisite:
1. You are expected to have the basic skills in handling
IBM-PC compatible computer running Windows 3.1, Windows 95/98 or
Windows 2000/Me/XP, including file handling operations using file
manager/Windows Explorer/ Netscape, basic text editing using Window's
notepad or MS Word.
2. The full time use of a PC desktop or laptop
3. An email address which you check daily.
4. You will need two burn two CDs, one for each project. If you
do not have a CD burner, these are available are Office Depot, Kinko's
and various other places.
5. The time and ability to go on a field trip either in a group
or by oneself.
6. The time and ability to work on two projects in a group or by
oneself.
7. The time and ability to check email daily
8. The time and ability to check the Professor's web daily
Both 8 and 9 are imperative to communicating
with the class
|
Check
list: |
|
1. Understanding how digital information moves down the digital
lines.
2. Transmission Media
3. Client/Server Computing
4. Information Architecture
5. Data Models
6. Protecting company information and Information Assurance. .
7. Understanding E-commerce and secure transactions.
8. Communication with digital ids, symmetric and asymmetric encryption
9. Legal issues
10. Setting up Policy and Procedures.
11. Systems Analysis and Design
12. Enterprise wide computing
13. Legacy Systems
14. What are the first TEN things I should do?
Please click on the Class Schedule on my web site
for a tentative outline of assignments.
|
Textbook:
|

Information Systems Management in Practice, 7/E
Barbara C. McNurlin, Writer, Information Technology
Ralph H. Sprague, University of Hawaii
Publisher: Prentice Hall
ISBN: 0-13-185471-2
Copyright: 2006 Format: Cloth; 672 pp
|
Office
Hours: |
Office hours for this class will be immediately after this class
for one hour:
For those of you wanting to see me during office hours,
you must make an appointment with me or the department assistants.
The assistants in turn will have to allocate an available office
in UPC, in our department, RB 250.
My office is located at BBC (A-II 120D) and is therefore
unreasonable and inconvenient for both students and myself to drive
up from UPC to BBC just to hold an appointment in the official FIU
allocated office.
Contact me first for an appointment or further assistance
by email (gk@fiu.edu) or see me in class. Email response time depends
on the volume of emails but I expect it to be within 1-2 working
days.
|
Course
grading: |
1. Exam 1 (20%)
2. Exam 2 (20%)
3. Exam 3 (20%)
4. Project 1 (10%)
5. Project 2 (10%)
6. Attendance (10%)
7. Class participation (10%)
8. Professional quality in the organization, completeness, neatness,
and timeliness of material handed in will be expected (including
exams).
9. During the semester there will be three exams and quizzes.
Quizzes are part of the class participation grade.
10. Make up exams - There will be no makeup exams - if you miss
an exam you will receive an F for that exam.
11. Extra work for better grade - There will be no extra work
assigned for an extra grade. Everyone will be treated on an equal
basis.
12. There will be NO exceptions on an INDIVIDUAL basis. If an
exception is requested for one student and it is granted, then
it will be announced in class and that exception will also be
valid for all other students.
|
Grading
Scale: |
95-100% |
A |
90-94.99% |
A- |
87-89.99% |
B+ |
84-86.99% |
B |
81-83.99% |
B- |
78-80.99% |
C+ |
75-77.99% |
C |
72-74.99% |
C- |
69-71.99% |
D+ |
66-68.99% |
D |
63-65.99% |
D- |
<63% |
F |
|
Religious
Holidays: |
Following FIU policy, the Academic Calendar for 2005-2006 includes
only official University holidays. References to specific religious
holidays have been excluded. In keeping with University policy,
faculty are encouraged to make accommodations for students who wish
to observe their religious holidays.
Students should make these requests known at the beginning of
the semester.
The FIU policy statement with reference to religious holy days
is printed on page 54 of the 2005-06 Undergraduate Catalog and
page 38 of the Graduate Catalog. The statement is copied herein
for your convenience:
Because there are some classes and other functions where attendance
may be considered essential, the following policy is in effect:
1. Each student shall, upon notifying his/her instructor,
be excused from class to observe a religious holy day of his/her
faith.
2. While the student will be held responsible for the material
covered in his/her absence, each student shall be permitted a
reasonable amount of time to make up any work missed.
3. No major test, major class event, or major University activity
will be scheduled on a major religious holy day.
4. Professors and University administrators shall not arbitrarily
penalize students who are absent from academic or social activities
because of religious observances.
For a listing of religious holidays you may visit
http://www.interfaithcalendar.org.
|
|
The best way to communicate with me is by email.
Emails
1. Subject line: When you send
an email, make sure that the subject line of your email starts
as per Example 1
that follows:
2. Carbon copies: If you would like to make sure
that you have sent important email correctly, send a "cc"
to yourself. Then if you do not get a copy back - you know there
is something wrong.
3. Requesting a receipt: If you want a receipt
for assignments, projects and important emails, activate your
receipt request in your email program. This is a simple procedure
and will cut down a lot of emails asking me -did you receive my
email Professor? If you are using Outlook Express for example,
Click on Tools, Options, Receipts and choose request receipt.
4. The time and date of your emails must be accurate
especially when there are deadlines. Your email starts off with
your computer's time and date. If this is incorrect by an hour,
then your email will arrive by an hour off. Therefore make sure
that the computer your are using, the lab computer, the office
computer, your friend's computer and your laptop and desktop have
an accurate time and date. Assignments that arrive late receive
only a fraction of the grade and assignments that do not arrive
at all, receive an incomplete until they arrive.
5. If the time or date is incorrect then this is what
you do: Move your mouse to the bottom right hand corner
of your monitor. Slide it over the time. This will give you the
time and date. If it is not accurate, right click on it. Adjust
date and time. Make sure Date, Time and Time Zone are correct.
6. Anti Virus: A good antiviral program is necessary.
Protect your computer. If your email or attachment contains a
virus, it will not be opened and will be deleted immediately.
7. All attachments being sent must be formats
that are supported. An example: MS Office, MS Word, MS Excel,
MS Access, MS PowerPoint, Notepad, WordPad, .jpeg, .mpeg, .wav,
.tiff, Corel Draw, .swf, .htm, FrontPage.
8. I do not support WordPerfect at this present
moment.
9. Spell check: Please activate and use it. Typos
and incorrect spelling does not make a good impression and sometimes
can confuse the reader.
10. Large files and attachments: Some email programs
have a limit on how large a file you can send through them. For
example, HOTMAIL has a limit of 1MB. If your attachment or file
is larger than 1 MB, your file will not be sent. You can either
compress your files with a zip or use another email service e.g.
Yahoo.com
11. Subject line: [ v e r y i m p o r t a n t ]
If your class, for example is CGS3300
this is what should go as a heading in your email subject line
CGS 3300
CGS3300/Pat Smith/Assignment 1
ISM 4220 Business Data Communications
ISM4220/Your
name /Subject...............for example
ISM4220/Pat Smith/Assignment 1
ISM 4990 Network Security
ISM4990/Your
name /Subject...............for example
ISM4990/Pat Smith/Assignment 1
International MBA
IMBA6830/Your Name/Subject
evening MBA6830
eveMBA6830/Your Name /Subject
Graduate Management Program MAN
6830
GMP 6830/Your name/Subject
executive MBA JAMAICA
JAMMAN6830/Your Name/Subject
If you are not attending a class
right now your subject line should start off with:
YOUR NAME/Subject
Example:
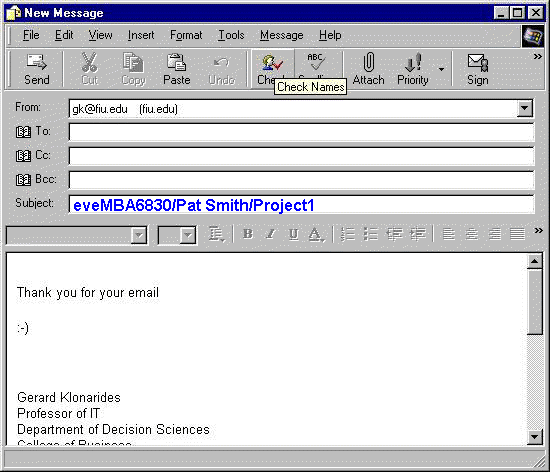
Telephone
calls
Please email me at gk@fiu.edu.
Do not call my department
to leave a message. The staff in the CBA are there to support
the faculty in their duties.
Faxes
Do not send faxes.
Dropping in: It is my pleasure to see you. However,
"dropping in" does not necessarily mean that there will
be enough time to see you or deal with a particular problem. So,
if your business is important make sure that you have emailed
me or spoken to me first.
|
|
|
|
|
|
Copyright © 2005 Gerard
Klonarides, Lecturer, DSIS, CBA, Florida International University.
|
 ISM6045 Syllabus
ISM6045 Syllabus